Expert in Comprehensive
World class Cybersecurity Solutions
Our industry-leading security solutions help you predict attacks, proactively respond to threats, ensure compliance, and protect data, applications, infrastructure and endpoints.
Too Many Alarms. Too Few Analysts
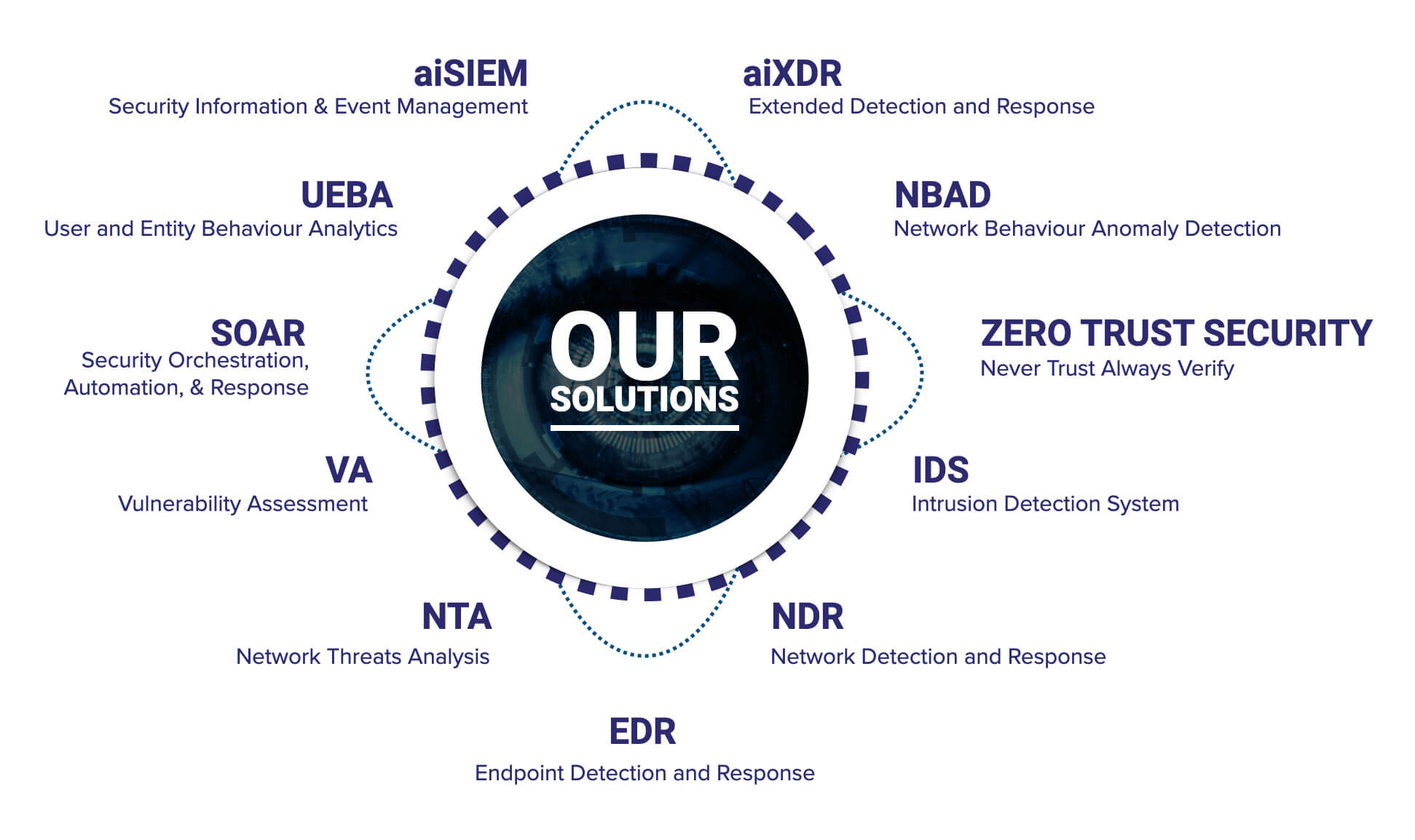
Zero Trust Security
Never Trust Always Verify
Zero Trust is a strategic cybersecurity approach for current digital corporate settings, which increasingly encompass public and private clouds..
Security Information & Event Management (SIEM)
Security Information and Event Management (SIEM) provides organizations with next-generation detection, analytics and response.
Network Detection and
Response (NDR)
NDR solutions are designed with Machine Learning and Data Analytics to detect cyber-attacks on corporate networks. These continuously analyze..
Extended Detection and
Response (aiXDR)
aiXDR protects your borders – remote office, cloud, office, or in transit with the help of razor-sharp analytics, led by Artificial Intelligence & Machine..
Vulnerability Assessment Solutions
Vulnerability Assessment is the process of analyzing vulnerabilities in IT systems. Its goal is to detect the system..
Intrusion Detection System
(IDS)
An Intrusion Detection System (IDS) is a system that monitors network traffic for suspicious activity and generate alerts..
User and Entity Behavior Analytics (UEBA)
UEBA is a form of cybersecurity solution or feature that detects threats by looking for such activities that differ from the..
Network Behaviour Anomaly Detection (NBAD)
An integral part Network Behaviour Analysis (NBA), continuously monitoring a propitiatory network to..
SOAR Technology
Cyber-attacks are continually increasing in number and sophistication than ever before. Organizations’ capacity to..
Network Threat Analysis
Network Threat Analysis is a vertical of cybersecurity which monitors the network traffic communications to identify..
Endpoint Detection & Response
Endpoint Detection Response (EDR), also known as Endpoint Detection and Threat Response (EDTR) is an endpoint security..
Advanced SIEM (aiSIEM)
Stop the breach and keep your business running at a low cost. aiSIEM provides round-the-clock protection for your network..
Take your threat detection and response to the next level
Password & Access Management
Attack Mitigation
Our Virtual CISO services can help you mitigate all types of cyber threats such as account compromise, unauthorized access, ransomware, network invasions, malware infections, sabotage, security policy violations, and much more.
Security Awareness Training
We offer everyone effective security awareness training that will stick with people as it is emotionally and logically relevant to them. Your Virtual CISO will improve security awareness within the organization.
Cloud Security Architecture
Microsoft 365 has more than 280 security settings. Amazon Web Services and Azure also offer hundreds of security configuration options – your virtual CISO takes care of ALL of them!
Securing IT Infrastructure
We help you transform the security of your IT infrastructure by implementing server and network device hardening, desktop hardening, network and web service security, data security, backups and more.
Vulnerability management
Are you aware of the number of vulnerable machines / apps on your network. We help you to set up and manage a vulnerability management program in order to gradually reduce existing vulnerabilities.
Email & Communications Security
Access to a corporate account can give a hacker access to any internal system. We implement secure authentication to ensure the integrity and confidentiality of your communications.
Breach simulation is an integral part of any information security program. You can rely on us to support you in initiating, carrying out and completing a penetration test.
Secure Software Development
Software development should be a quick, efficient, and secure process. Our virtual CISO services help you integrate security into the design, development, testing, integration and delivery of your code.
Security Policies and Procedures
Policies and procedures are the laws that govern a company’s business. We create dynamic and breathing documents that help our customers organize and structure their security procedures
Secure Remote Access
Remote access to data is not limited to VPN. One aspect of remote access is working securely from home. However we also take care of third-party partners and outsourced employees, suppliers and guests.
Zero Trust Networking
That’s why we’re expanding your defense beyond VPN and adding zero trust as your primary defense principle.
Advanced Endpoint Security
Antivirus is just one of 12 controls we implement to protect endpoints from advanced hacker attacks. We prevent the exploitation of these devices through malicious documents, scripts, zero-day vulnerabilities and more.
Security Monitoring
We help you transform the security of your IT infrastructure by implementing server and network device hardening, desktop hardening, network and web service security, data security, backups and more.
And Much More
As our customers’ teams, infrastructure, applications used, and business goals are unique, we create and run every information security program for them in different manner. We often expand our services to serve them better.
Related products and services
Penetration Testing
Penetration Testing, otherwise known as Pentesting, identifies cyber security issues by simulating attempts to defeat safeguards. You can rely on us to support you in initiating, carrying out and..
Open Threat Management Platform - CCE | EDR Agent | APE | aiXDR
OTM Platform proactively and confidently raises and eliminates only qualified cybersecurity threats based on available information and knowledge from..
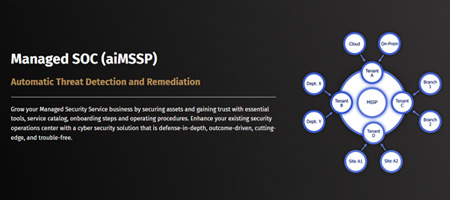
Managed SOC aiMSSP - Automatic Threat Detection and Remediation
aiMSSP is the most adaptable Managed Detection and Response platform on the market, combining a SOC Dashboard with a defense-in-depth cybersecurity..
Detect Ransomware in Initial Steps and Stops it - aiSIEM and aiXDR
Targeted ransomware attacks against government bodies, schools, universities, corporations, service providers, and even small-medium businesses have..